40 an rfid label on a box is an example of what type of physical security detection method?
How do RFID and RF tags work? - Explain that Stuff Photo: An example of the kind of RFID tag used in book labels. It helps with automated stock control and (in some systems) might double-up as an anti-theft device. You can often see these by holding library paperbacks up to the light. This tag is a UPM Raflatac RaceTrack that can hold up to 1 kilobyte (1024 characters) of information. What are RFID Tags? Learn How RFID Tags Work, What They're ... - Camcode RFID tags are a type of tracking system that uses smart barcodes in order to identify items. RFID is short for "radio frequency identification," and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.
en.wikipedia.org › wiki › Radio-frequency_identificationRadio-frequency identification - Wikipedia Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter.When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader.

An rfid label on a box is an example of what type of physical security detection method?
achieverpapers.comAchiever Papers - We help students improve their academic ... We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order What is RFID? | Zebra RFID stands for radio frequency identification. It is an automatic identification technology whereby digital data is encoded in an RFID tag or "smart label" and is captured by a reader using radio waves. Put simply, RFID is similar to barcode technology but uses radio waves to capture data from tags, rather than optically scanning the barcodes ... Comparison of RFID and NFC - RFID LABEL Many people worry about their data's security since hackers can tap into the wireless communication process and steal their personal information. If we look at RFID, it has a more extended range of operation, which means that the RFID tag and scanner can be present far away from each other, and the transfer of information can still take place.
An rfid label on a box is an example of what type of physical security detection method?. Network+ guide to Network Exam 3 You'll Remember | Quizlet Asset tracking tagging An RFID label on a box is an example of what type of physical security detection method? when it exceeds the medium's maximum packet size. At what point is a packet considered to be a giant? Class of Service utilizes 8 levels of priority By default, Active Directory is configured to use this security protocol What is an RFID Label | Zebra In essence, an antenna is what allows the RFID tag to communicate with the RFID reader. The antenna receives signals from an RFID reader and sends data back to the reader. Antennas come in many shapes and sizes with the design being an important factor as it affects how the data is transmitted and read. achieverstudent.comAchiever Student: The best way to upload files is by using the “additional materials” box. Drop all the files you want your writer to use in processing your order. If you forget to attach the files when filling the order form, you can upload them by clicking on the “files” button on your personal order page. Ch9 network Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. On a Linux based system, what command can you use to create a hash of a file using SHA-256? ...
Ch. 9 Quiz CTS1134 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised. RFID 101: What's the Difference Between Active RFID ... - GuardRFID By design, Passive RFID tags are smaller, thinner and are of a more flexible composition than Active RFID tags, in addition to lasting upwards of 20 years or more. The slightly lower price point per tag can (in some cases), make it a more affordable solution for some end users, depending on the overall use case. Radio Frequency Identification (RFID) | FDA Active RFID tags are powered by batteries. RFID tags can store a range of information from one serial number to several pages of data. Readers can be mobile so that they can be carried by hand, or... 7 Powerful Examples of How RFID Technology can be Used in Retail RFID tag applications — RFID tags (specifically external tags vs. embedded) can be applied anywhere in the supply chain — at the supplier, distribution center, or retail store — each with ...
Network+ 8th Edition Chapter 9 Flashcards - Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging asset tracking tagging 12. RFID Inlays, RFID Tags, RFID Labels - What is the Difference? 2.RFID Label. An RFID label contains all the elements of the tag. Just like an RFID inlay, a label includes an antenna, chip, and substrate. They are also called smart labels. An RFID label is an RFID inlay embedded on paper. It is an ideal method to track products during shipping. 3. Assignment Essays - Best Custom Writing Services Get 24⁄7 customer support help when you place a homework help service order with us. We will guide you on how to place your essay help, proofreading and editing your draft – fixing the grammar, spelling, or formatting of your paper easily and cheaply. Chapter 9 -- Network II Flashcards & Practice Test | Quizlet A) Polymorphic malware can change its characteristics every time it is transferred to a new system. B) Polymorphic malware is designed to activate on a particular date, remaining harmless until that time. C) Polymorphic malware is software that disguises itself as a legitimate program, or replaces a legitimate program's code with destructive code.
Achiever Student: The best way to upload files is by using the “additional materials” box. Drop all the files you want your writer to use in processing your order. If you forget to attach the files when filling the order form, you can upload them by clicking on the “files” button on your personal order page.
assignmentessays.comAssignment Essays - Best Custom Writing Services Get 24⁄7 customer support help when you place a homework help service order with us. We will guide you on how to place your essay help, proofreading and editing your draft – fixing the grammar, spelling, or formatting of your paper easily and cheaply.
Radio-frequency identification - Wikipedia Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter.When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, …
Introduction to RFID Labels: A Beginner's Guide - RFID LABEL RFID labels or smart tags are used to track, trace, and monitor retailing products, inventory items and consumer assets. The presence of smart labels ensures RFID technology handles multiple applications, including: Customer service and access control Vehicle tracking Cargo and supply chain logistics Library systems Patient management
What is RFID There are three types of RFID-related events: 1. A New Tag event occurs when a tag appears to a reader for the first time. 2. A Visibility Changed event occurs when the visibility of a tag changes for a read point. 3. A Tag Not Visible event occurs when a tag is no longer visible to any read point.
Course Help Online - Have your academic paper written by a … We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order
› 8538075 › Handbook_of_MaintenanceHandbook of Maintenance Management and Engineering Enter the email address you signed up with and we'll email you a reset link.
Sysmac Studio Update Information | OMRON Industrial Automation Solved the problem that an invalid text string was displayed when running the simulator if a specific text string was set for Label. Solved the problem that the performance was lowered if the build operation was executed while the global event window was open. Reduced the restrictions of the reserved words.
PDF Intro to Radio Frequency Identification Systems and RFID Tags - omni-id Applicator A label-printing device to print and apply pressure-sensitive labels to RFID tags. Pressure sensitive labels consist of a substrate and an adhesive. Used for shipping, content, graphic images or complying with standards such as UPC or GS1. Asset Tracking The most common RFID tag application. RFID asset tagging increases asset ...
Achiever Papers - We help students improve their academic standing We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order
› dfars › part-252-solicitationSOLICITATION PROVISIONS AND CONTRACT CLAUSES - Acquisition (3) Apply other information systems security measures when the Contractor reasonably determines that information systems security measures, in addition to those identified in paragraphs (b)(1) and (2) of this clause, may be required to provide adequate security in a dynamic environment or to accommodate special circumstances (e.g., medical ...
What is RFID and how does it work? - TechTarget The RFID reader is a network-connected device that can be portable or permanently attached. It uses radio waves to transmit signals that activate the tag. Once activated, the tag sends a wave back to the antenna, where it is translated into data. The transponder is in the RFID tag itself.
RFID Tags, What Exactly are They and How do they Work? - IRDA.org RFID tags work by using a microchip and an antenna to receive and transmit information. People sometimes refer to this as an IC or integrated circuit. The RFID tags comes in two main types: these are passive and battery-operated. Just as the name suggests, RFID tags that are battery-operated use an onboard battery as their power supply.
Chapter 9 Study Set Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? A.) motion detection technology B.) video surveillance via CCTV C.) tamper detection D.) asset tracking tagging. D.) asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate
RFID Labels: Definition and Applications - Dipole RFID The RFID label assigned to each participant allows controlling the route he/she takes while timing him/her. These labels are disposable, and allow precise timing without causing any discomfort to the athlete. They can be worn attached to the back, sports shoes, or other clothing items worn by the runner.
RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database.
PART 252 - SOLICITATION PROVISIONS AND CONTRACT CLAUSES … (3) Apply other information systems security measures when the Contractor reasonably determines that information systems security measures, in addition to those identified in paragraphs (b)(1) and (2) of this clause, may be required to provide adequate security in a dynamic environment or to accommodate special circumstances (e.g., medical ...
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging d. asset tracking tagging 12.
A Beginner's Guide to The Types of RFID Tags - RFID LABEL Low Frequency (LF) Low frequency (LF) RFID tags work on frequencies ranging from 30 kHz to 300 kHz. The LF reader can detect the tag from a distance of about 10 cm, which is a disadvantage compared to other tags (HF and UHF). However, LF RFID tags are much less susceptible to interferences from other sources, such as metal particles and liquids.
What is RFID? | The Beginner's Guide to How RFID Systems Work Radio Frequency Identification (RFID) is the wireless non-contact use of radio frequency waves to transfer data. RFID systems usually comprise an RFID reader, RFID tags, and antennas. How Does RFID Work? Tagging items with RFID tagsallows users to automatically and uniquely identify and track inventory and assets.
coursehelponline.comCourse Help Online - Have your academic paper written by a ... We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order
The Handbook of Logistics and Distribution Management Enter the email address you signed up with and we'll email you a reset link.
Ch 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. In the typical social engineering attack cycle, what occurs at Phase 3? The attacker exploits an action undertake by the victim in order to gain access.
What is an RFID Label | Zebra With RFID experiencing quick growth and adoption across a wide range of applications within Manufacturing, Transportation & Logistics, and Healthcare. RFID labels represent a key component in the success of any RFID solution. What are the components of an RFID Label? a.) Chip - This makes up an inlay along with the antenna.
Handbook of Maintenance Management and Engineering Enter the email address you signed up with and we'll email you a reset link.
Subscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today.
Comparison of RFID and NFC - RFID LABEL Many people worry about their data's security since hackers can tap into the wireless communication process and steal their personal information. If we look at RFID, it has a more extended range of operation, which means that the RFID tag and scanner can be present far away from each other, and the transfer of information can still take place.
What is RFID? | Zebra RFID stands for radio frequency identification. It is an automatic identification technology whereby digital data is encoded in an RFID tag or "smart label" and is captured by a reader using radio waves. Put simply, RFID is similar to barcode technology but uses radio waves to capture data from tags, rather than optically scanning the barcodes ...
achieverpapers.comAchiever Papers - We help students improve their academic ... We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order


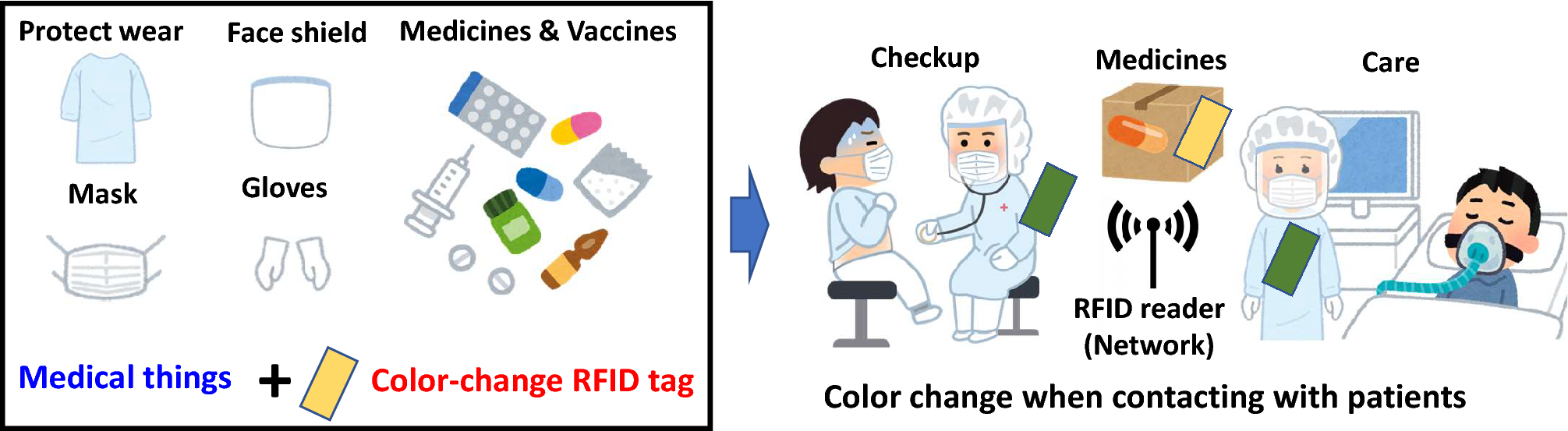




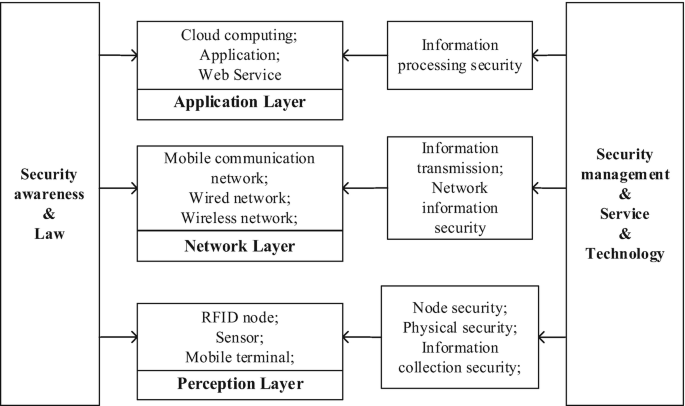









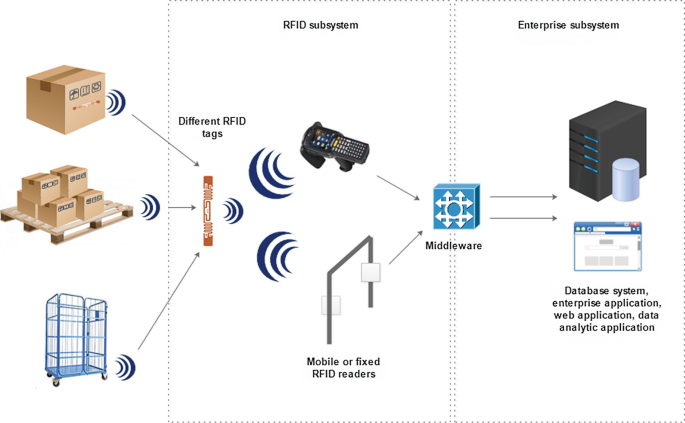
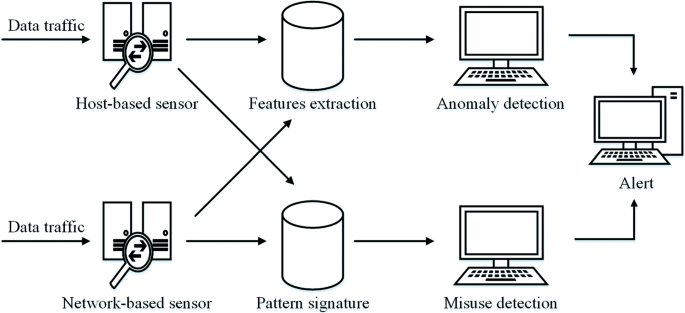
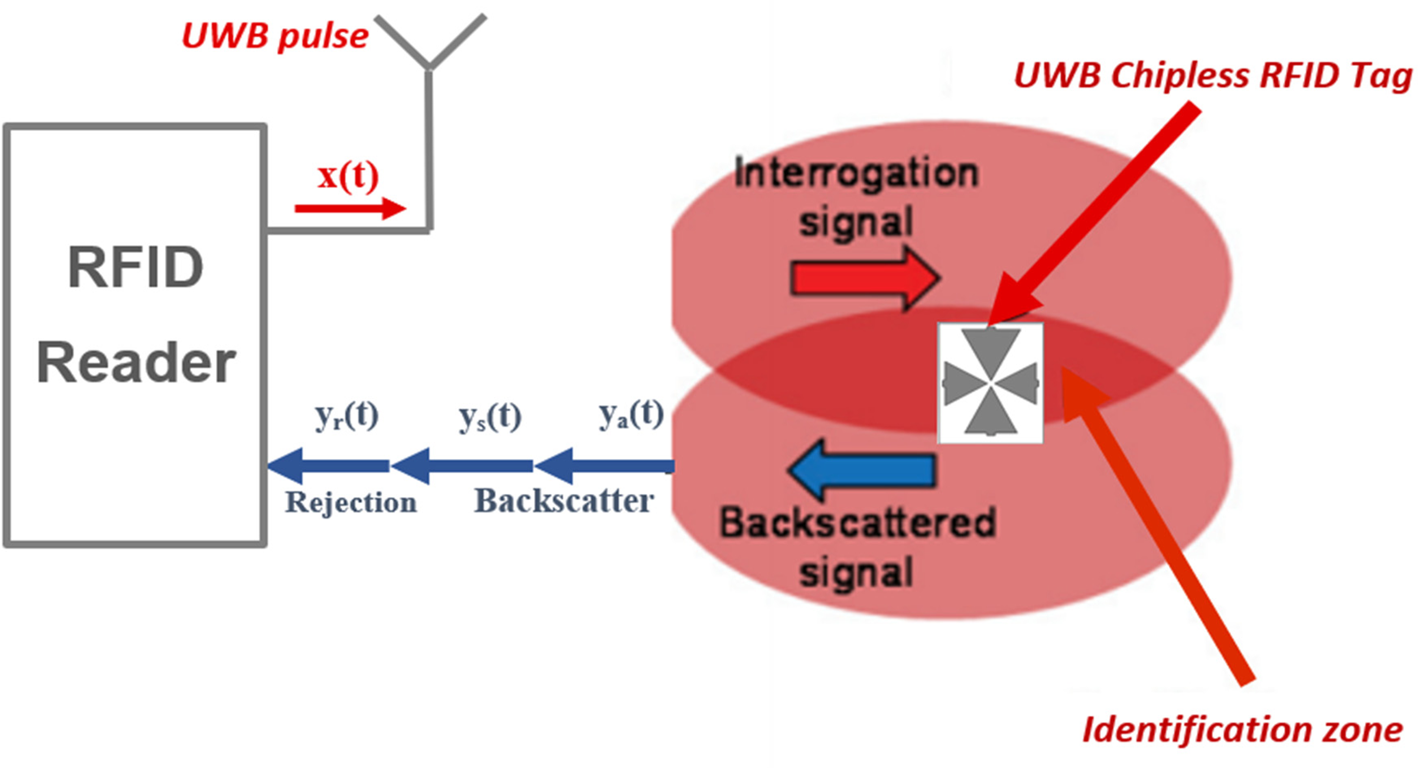
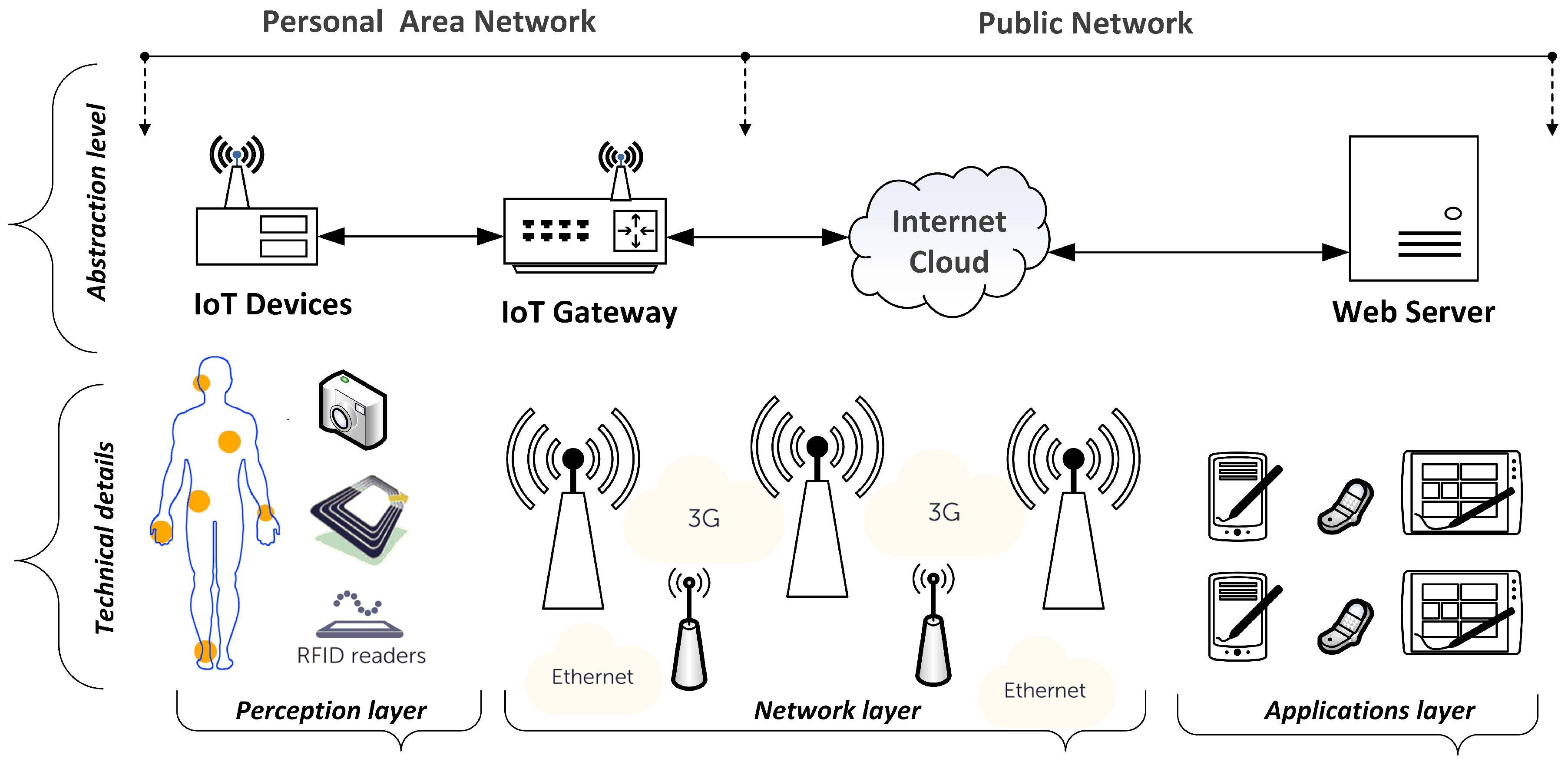
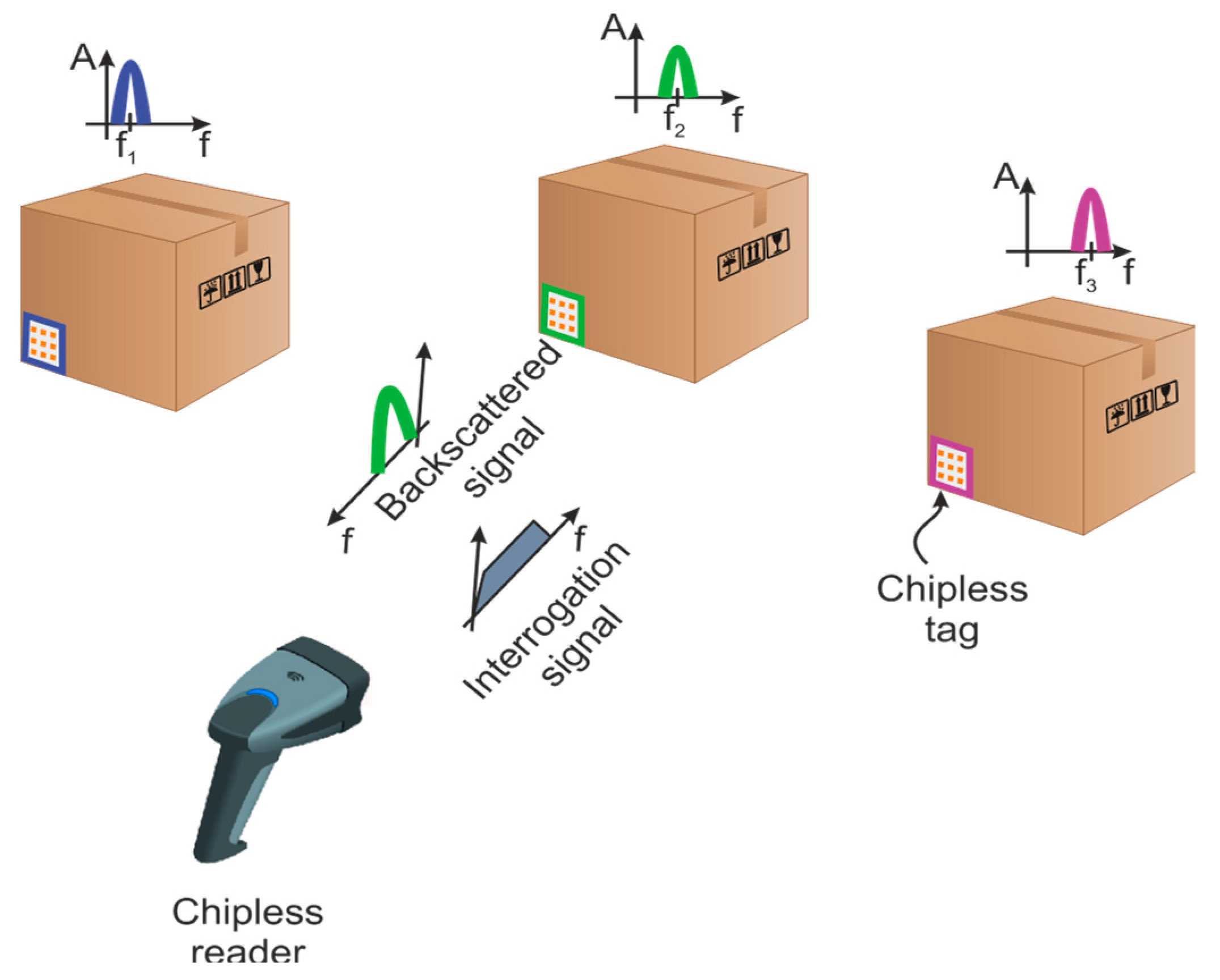

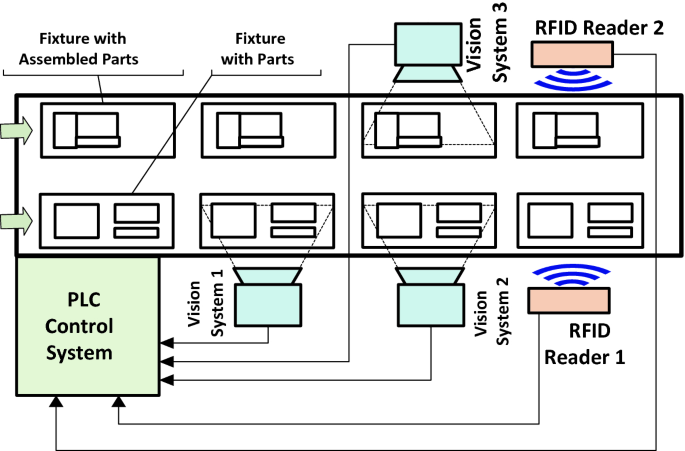
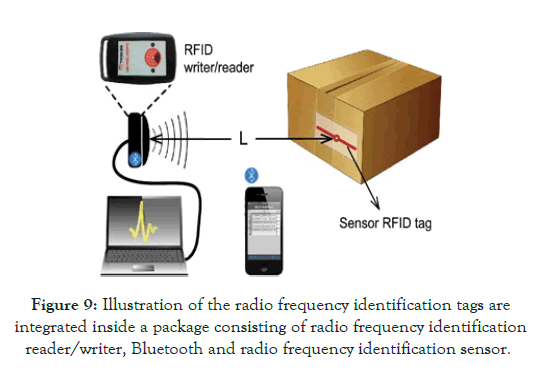

Post a Comment for "40 an rfid label on a box is an example of what type of physical security detection method?"